Encrypt Data
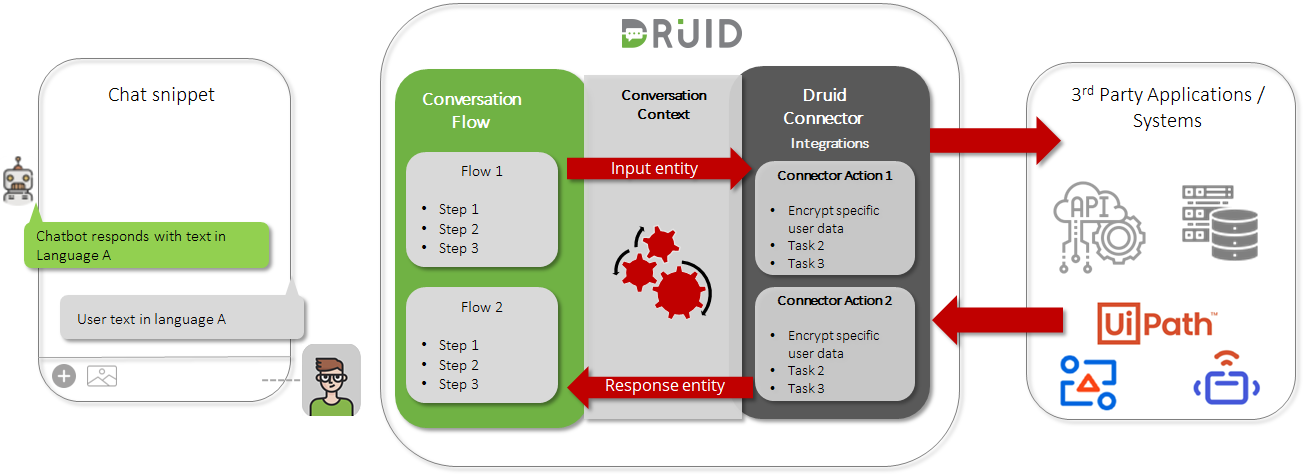
Users use chatbots in communication with financial institutions, healthcare assistants, airport companies, online shops, and many others. There are cases when third party applications require specific user information (sensitive or not, e.g. user account credentials, client ID, client name, etc.) to be transmitted in a secure way.
Bot authors can now achieve this by designing their chatbots to encrypt the data transmitted by Druid connectors using the AES GCM encryption algorithm.
Constructed from the Advanced Encryption Standard (AES) algorithm with a block size of 128 bits, AES with Galois/Counter Mode (AES-GCM) is a block cipher mode of operation that provides high speed of authenticated encryption and data integrity.
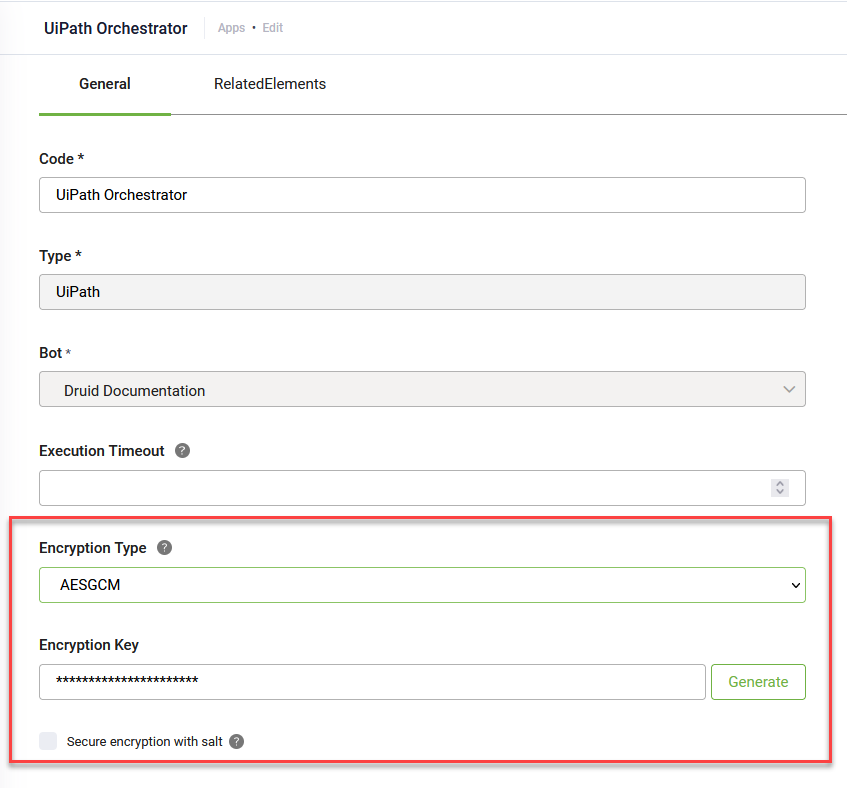
On the connector app, you select the encryption type AES CGM and generate an encryption key.
If you want to encrypt the data with a higher level of security, on connector apps, select Secure encryption with salt. By doing so, Druid will alter the Druid fields with a random 64-bit salt and then will encrypt the data using the AES CGM algorithm and the encryption key from the connector app specified in the Encrypt Data integration task. Further details are provided later on in this section.
Encrypt data on the connector by using the Encrypt Data integration task
By using the Encrypt Data task, you ensure that unauthorized parties cannot alter or spoof the data Druid transmits to external systems.
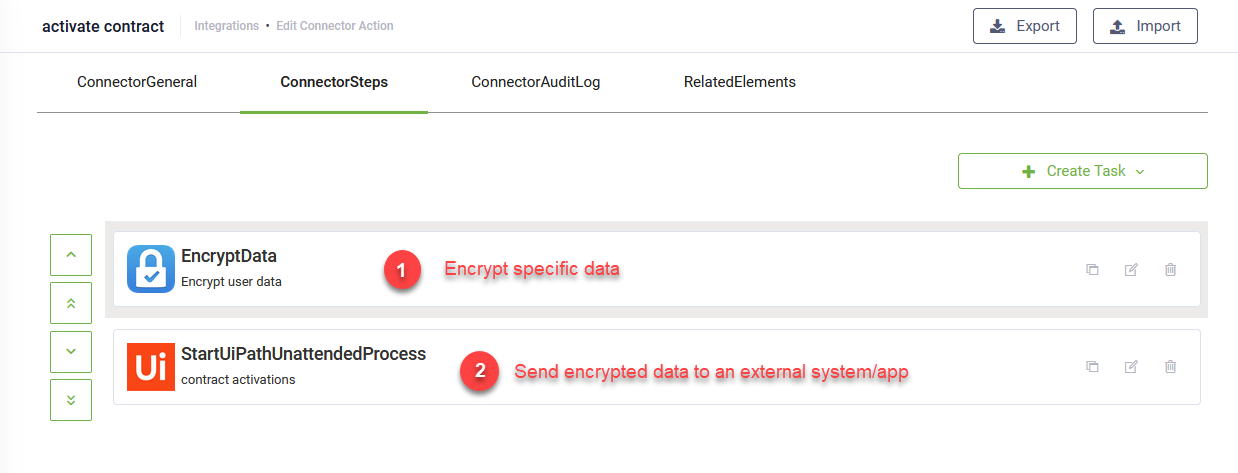
When defining the connector actions, you first encrypt the data based on your needs by using the Encrypt Data integration task, and then use that data on subsequent tasks.
If you want to add data encryption on existing connector actions, add the Encrypt Data task, configure it and then use the drag and drop functionality to make it the first integration task to be executed in that connector action.
To add an Encrypt Data integration task, go to the desired connector action, click the Create Task button, click Security and select Encrypt data.
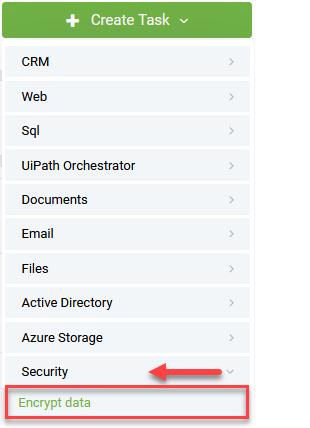
The Encrypt Data configuration page appears.
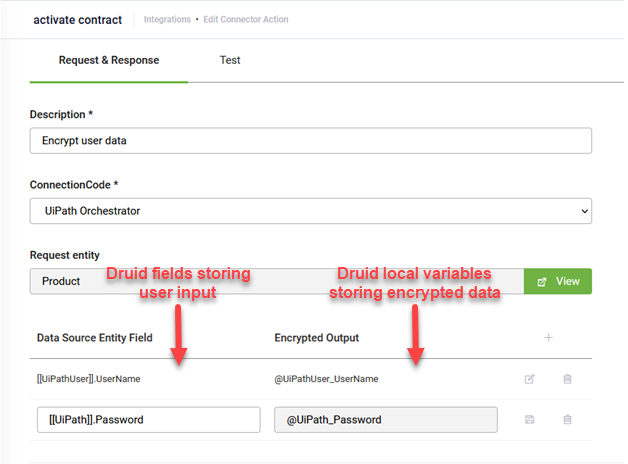
Provide a Description and from the ConnectionCode field, select the desired connector app.
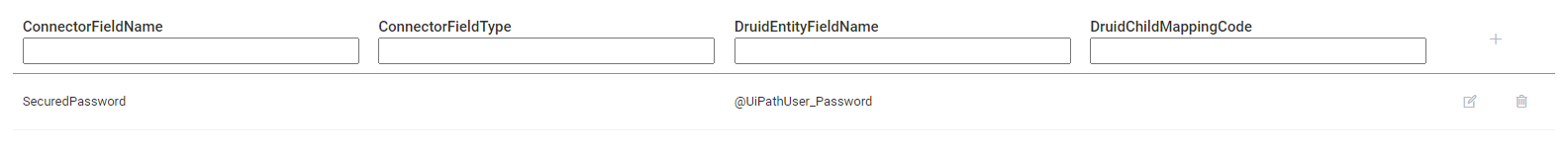
Provide the Druid entity field(s) you want to use as input for data encryption (fields from the request entity set on the connector action), regardless if they are sensitive or not. Then, the encryption task will output the encrypted data in automatically created local variables, which should further be used as input data in the subsequent connector task(s); the local variables only exist during the runtime of the integration (connector action), so until the last task from the action is completed.
Druid uses the following naming rule for local connector variables: @<entityName>_<entityField> corresponding to the Druid entity field selected in the left column, [[<entityName>]].<entityField>. For example, Druid automatically generates the local connector variable @Account_Password for entity field [[Account]].Password.
Save the integration task, by clicking the Save & Close button.
To further use the encrypted data in the subsequent tasks, simply specify the local variables generated by the encryption task, in the DruidEntityFieldName field on the Request tab of the task.
When Druid executes the connector action, it will use the AES CGM encryption algorithm and the encryption key from the connector app specified in the Encrypt Data integration task and will apply encryption on data from mapped input fields, into auto-generated local connector variables.
In case the input data is stored in sensitive entity fields, Druid first decrypts the sensitive data using its proprietary encryption/decryption algorithm, and then encrypts the data using the algorithm selected on the connector app (AES GCM, at this stage).
If encryption with salt (Secure encryption with salt option) is set on the connector app, then Druid will first alter the value stored in the Druid field with a random 64-bit salt and afterwards encrypts the data using the AES CGM algorithm and the encryption key from the connector app specified in the Encrypt Data integration task.
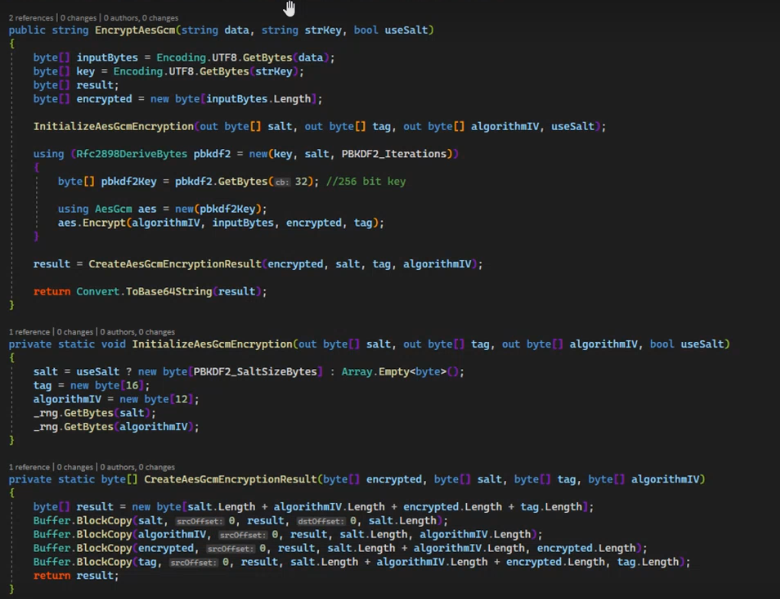
Druid AES GCM encryption uses Rfc2898DeriveBytes with 10000 iterations to generate a PBKDF2 pseudo-random 256 bit key.
Only the input data that is held in sensitive Druid entity fields (with “Holds Sensitive Data” true) will be anonymized from connector logs and conversation history.
Decrypt encrypted information received from Druid connectors
The clients receiving the data will have to develop code to decrypt the data using the AES CGM algorithm and the encryption key generated in Druid on the connector app.
If encryption with salt (Secure encryption with salt option) is set on the connector app, then Druid will first alter the value stored in the Druid field with a random 64-bit salt and afterwards encrypts the data using the AES CGM algorithm and the encryption key from the connector app specified in the Encrypt Data integration task.
Druid AES GCM encryption uses Rfc2898DeriveBytes with 10000 iterations to generate a PBKDF2 pseudo-random 256 bit key.
If secure data encryption with salt is set on the connector app, the client is required to perform additional decryption steps.